With social media and tech centering our lives more than ever as we move towards further material advancements, cyber threats loom over our heads like a vulture over carcasses on the ground.
So whether watching TV shows on your favorite channels like DStv or other regions on earth or using social media to promote your business, one needs to be highly aware of cybercriminals that cautiously wait to target their victims online at any second.
Malware:

In simple words, malware is any virus, trojan horse, worm, spyware, ransomware, etc., which cybercriminals install or deliver to their victim’s device. To combat such malware, one should take several steps to ensure their protection, like installing legit antivirus software, avoiding clicking on any unknown or fishy links, and updating your device regularly.
Phishing:
Phishing, also known as online impersonation, is done by pretending to be someone trusted online to trap/attack another person and send them fake messages or emails. Often, these messages or emails contain links that, through clicking, can help the cybercriminal hack their victims’ devices or social accounts. To keep yourself secure from such an attack, it is crucial to turn on two-factor authentication on your bills, update your passwords regularly, use the latest tools for protection, and intensely scrutinize the texts to catch any spelling or other formatting errors.
Man-in-the-Middle Attack:
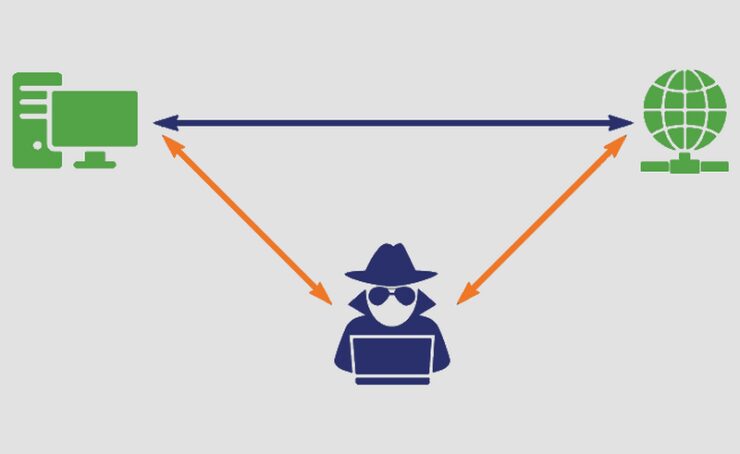
This is the type of cyber attack where the cybercriminal hijacks the private line of communication between two or more people, eavesdrops on their conversation, and attempts to steal their data. There is a higher chance of that happening to you if you use public Wi-Fi or do not use encryption on your devices. So, make sure you avoid doing that to keep yourself and the one you are communicating with on the safer side.
Crypto jacking:
As its name suggests, crypto jacking hijacks another person’s device for mining cryptocurrency. It is done by prompting the victim to click on any harmful link or having them open a website filled with malware. By doing so, one gains significant access to another person’s data, leaving them free to misuse it and mine all the cryptocurrencies in it. Keep yourself safe from such attacks by updating your devices, installing anti-theft or anti-malware software, and installing an ad blocker.
Password Attack:
This is an attack where the cybercriminal uses multiple tools to crack open accounts by uncovering your passwords. To ensure your data remains secure, keep updating your passwords regularly, use a strong password, and use different passwords on every platform.
Insider Threat:

This is a much harder-to-combat cyber threat as, judging by its name, it is an act done by people inside any organization to commit cybercrimes against it. This exposes the company and its employees to a higher security threat as most of their data is open to the staff, especially in the IT department. To ensure that this doesn’t happen to you, spread ample awareness in the organization you work in to spot insider threats and limit access to data to the staff working at IT to ensure the employees’ protection.
Final Thoughts:
To sum it up, these are among the most common cyber threats that one should always be aware of when using technology and social media. Knowing about them and how to combat them will help secure your data, finances, and other valuable information online. While not everyone faces these issues in their lives, one can never be too safe, and taking measures to keep all your devices and data safe would help you avoid unexpected cyber threats.

